View intranet boundary traffic
This article describes how to view the traffic at the intranet boundary. You can use this traffic information to understand network security.
Before using the Internet border traffic function, you need to confirm that you have purchased and deployed a Traffic Security Monitor (ISW) - for full traffic audit and analysis control of Internet border inbound and outbound traffic.
Context
Through traffic information, you can identify abnormal intranet traffic and block malicious access sources through the blocking function.
Procedure
On the product management page, select the Traffic Security Monitor button.
On the Traffic Security Monitor Console page, click the Internal Network Border tab.
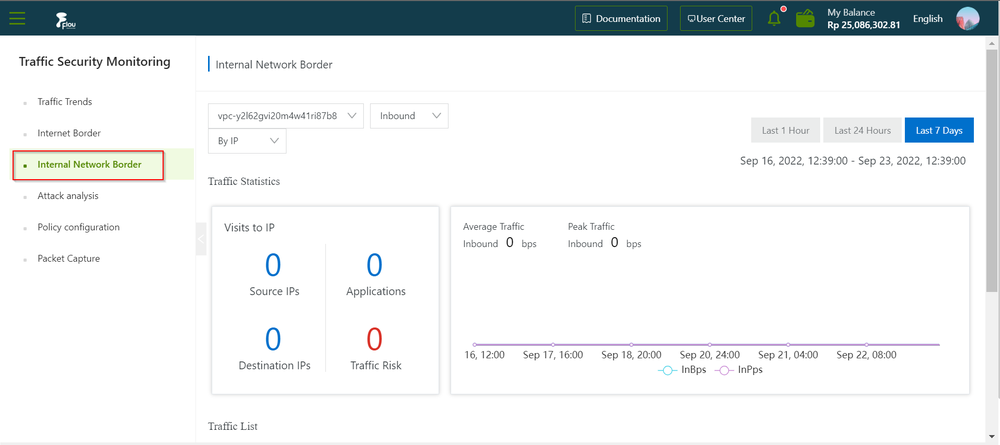
On the Internal Network Border section, review the Traffic Statistics information.
Note:- You can choose your time range on the Internal Network Border section by clicking the options near the top right corner (Last 1 hour, Last 24 hours, or Last 7 days).
- You can set the traffic filters to pinpoint relevant data.
- You can set the traffic direction to be viewed, both inbound and outbound directions are supported.
- You can view intranet boundary traffic by IP and by application. You can select the VPC instance name from the drop-down list for detailed analysis