Configure tamper protection
The Server Security feature allows you to configure tamper protection for web pages.
Context
- For each server, you can add a maximum of 10 directories for protection.
- If you want to add directories that are on a Linux server, the directories must meet the following requirements: The size of each directory does not exceed 20 GB. Each directory contains no more than 3,000 folders. The number of directory levels does not exceed 20. The size of each file does not exceed 3 MB.
- If you want to add directories that are on a Linux server, the directories must meet the following requirements:The size of each directory does not exceed 20 GB. Each directory contains no more than 3,000 folders. The number of directory levels does not exceed 20 . The size of each file does not exceed 3 MB.
- Before you add a directory for protection, make sure that the directory meets the preceding requirements.
- We recommend that you exclude file formats that do not require protection, such as LOG, PNG, JPG, MP4, AVI, and MP3. Multiple file formats can be separated by semicolons (;).
Procedure
On the product management page, select the Server Guard button.
On the Server Guard page, click the File Tamper Protection tab.
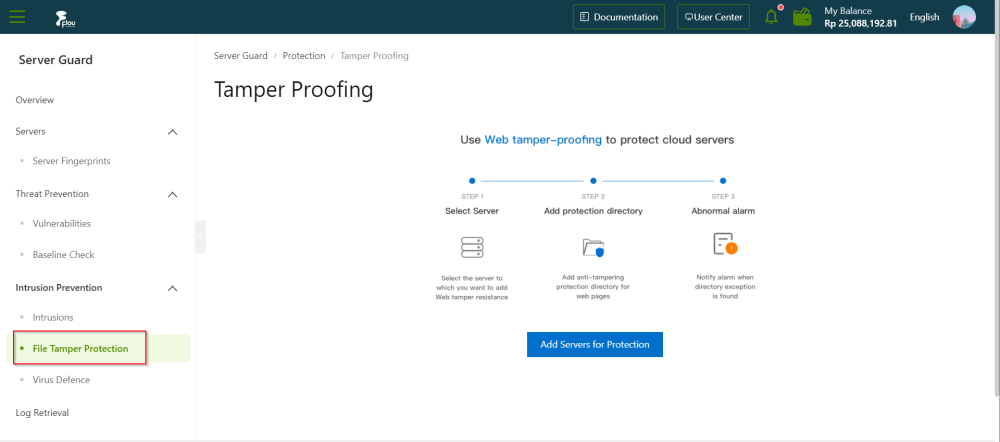
On the Tamper Proofing page, click the Add Servers for Protection button.
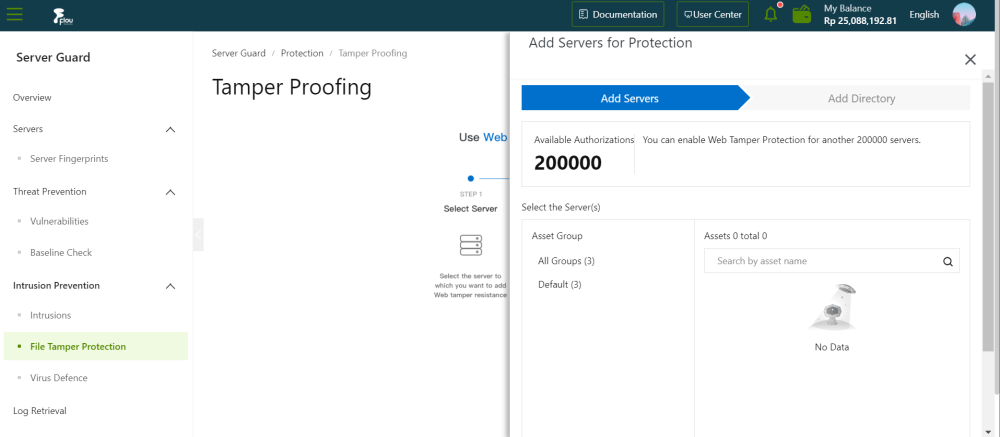
On the Add Servers for Protection section, select a server.
On the Add Servers for Protection section, click the Next button.
On the Add Servers for Protection section, configure the directory.
Select a protection mode
The settings of other parameters vary based on the protection mode. You can select Whitelist Mode or Blacklist Mode.
In whitelist mode, tamper protection is enabled for the specified directories and file formats.
In blacklist mode, tamper protection is enabled for the subdirectories, file formats, and files that are not specified. By default, Whitelist Mode is selected.
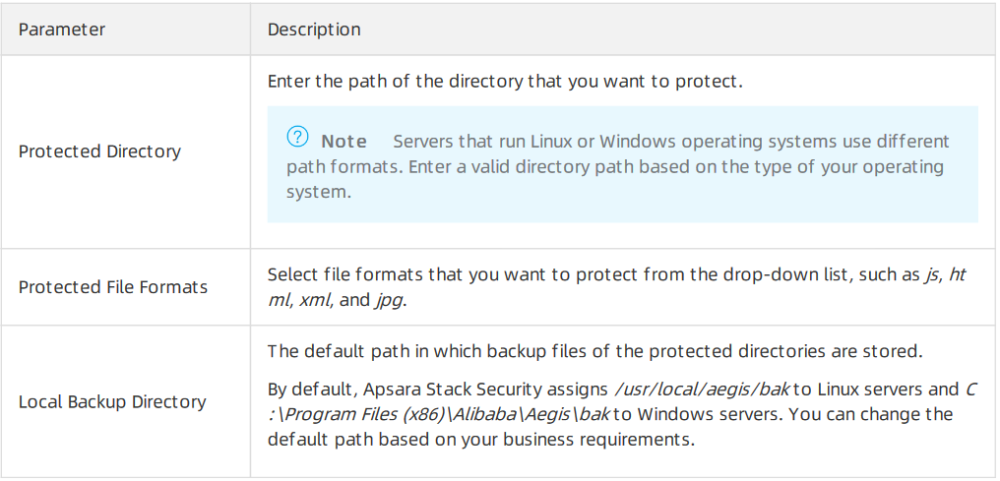
The following table describes the parameters that you must configure if you select Whitelist Mode.
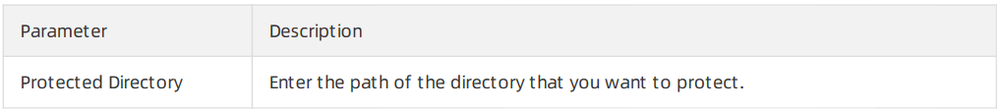
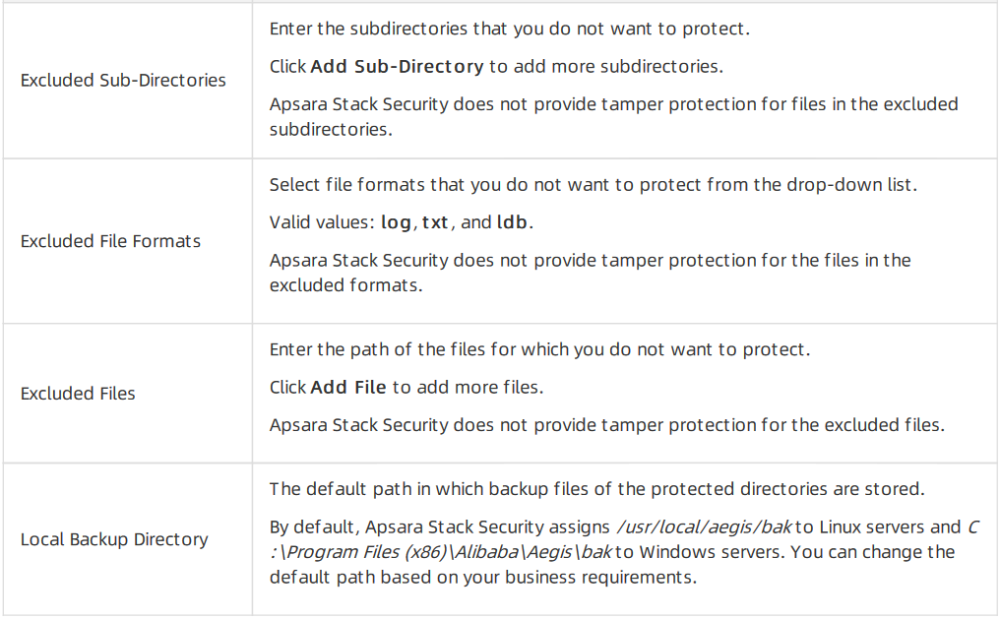
The following table describes the parameters that you must configure if you select Blacklist Mode.
On the Add Servers for Protection section, click the Enable Protection button.
Note: After you enable this feature for a server, the server is displayed on the Management tab of the Tamper Protection page.
By default, tamper protection is in the Off state for the server. To enable tamper protection for the server, you must turn on the switch in the Protection column on the Tamper Protection page.
On the Tamper Protection page, find the newly added server. Click the Management tab and turn on the switch in the Protection column to activate protection.
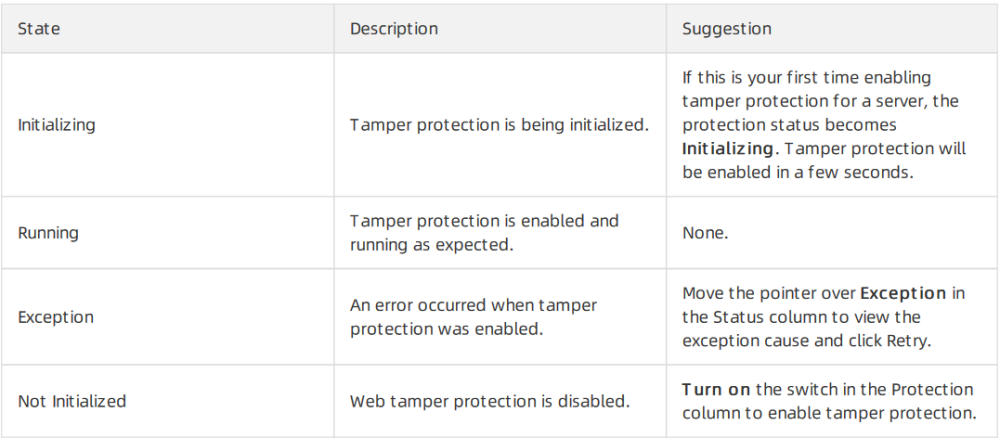
Note: By default, tamper protection is in the Off state for the server. To enable tamper protection for the server, you must turn on the switch in the Protection column on the Tamper Protection page. After activating protection, the server's status should change to Running. If the status shows Exception, hover over the word to view the reason and click Retry to attempt enabling protection again.
You can go to the Alerts page and select Web page Tampering from the alert type drop-down list to review the alerts generated upon tampering events
Note: Tamper protection does not take effect immediately after you configure the protected directory, and you can still write files to the directory. In this case, you must go to the Management page, disable Protection for the server where the directory is located, and then enable Protection again.
Handling suggestions for abnormal protection states